Von Michael Wager
As cybersecurity threats continue to evolve, the need for robust vulnerability management tools has never been greater. One such powerful open-source tool is OWASP’s DefectDojo. At secureIO, we do not only use DefectDojo to manage and track vulnerabilities, but we also actively contribute to its development. This blog post will introduce the features of the tool and also highlight our recent contributions.
What is OWASP DefectDojo?
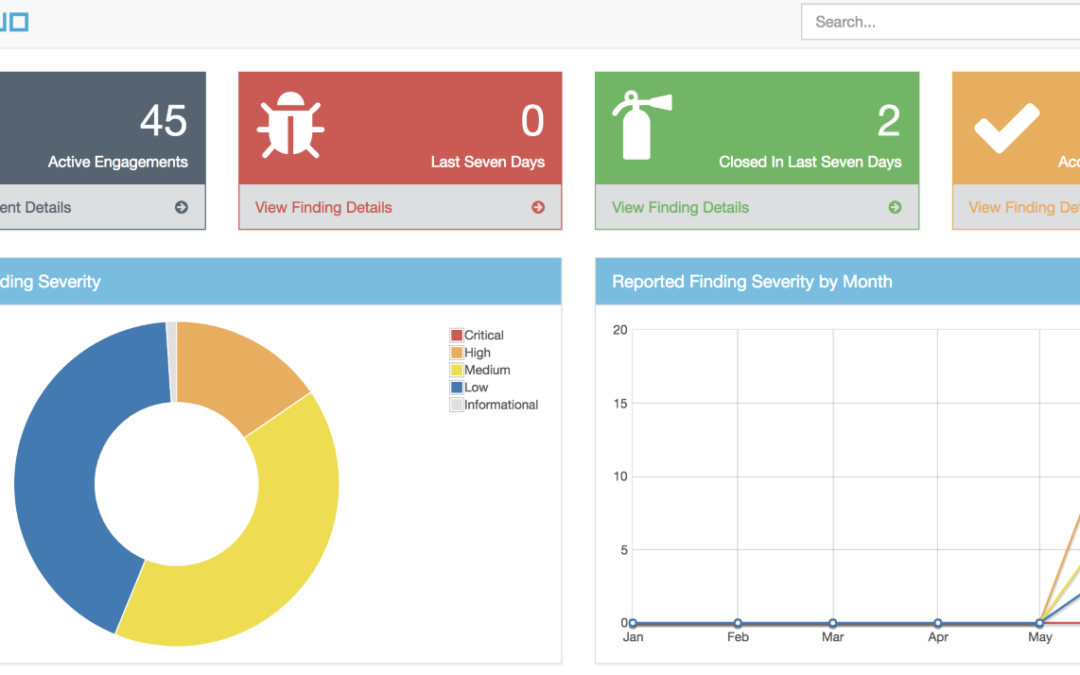
OWASP DefectDojo is an open-source application vulnerability management tool that helps security teams track, manage, and report on vulnerabilities discovered in their environments. It simplifies the complex process of vulnerability tracking and provides valuable insights through comprehensive dashboards and reports. Key features include:
- Centralized vulnerability management: Results of scanner, manual Penetration-Tests etc will be imported centrally
- Detailed reporting and analytics: be able to quickly communicate a products security stance
- Integrations with various scanning tools: supports >170 Scanners out of the Box (like Checkmarx, Nessus, BurpSuite, etc.)
- Role-based access control
- Risk acceptance: change status of findings (e.g. false positives, accept risk etc)
- Deduplication: compares findings to automatically identify duplicates
- Service Level Agreement (SLA): allows you to maintain your security SLAs and automatically remind teams whenever a SLA is about to get breached, or is breached
Our Contributions to DefectDojo
secureIO is always trying to give back to the community, that’s why we have a public GitHub Organization where all our open-source projects are hosted. See github.com/secureIO-GmbH.
After introducing and setting up DefectDojo for a large enterprise customer, we found that it did not support a certain scanner used by their teams, so we quickly aligned with the OWASP community and created a pull request to create a new Parser: https://github.com/DefectDojo/django-DefectDojo/pull/10522. This parser enhances the tool’s ability to interpret and import findings from an additional security scanner called Kiuwan, further expanding its versatility and usability.
More Open Source Engagement at secureIO
Some months ago, we also started our own open-source project: Vulnerability-Heatmap. The idea comes from the need to visualize security vulnerabilities across multiple projects in a heatmap representation. The orchestration and tracking has become quite complex, especially for central security teams in large enterprises dealing with a multitude of distributed teams. The heatmap is built for the ease of adaptation by technology management and development roles to identify the critical outliers within the organization. The different views of the heatmap allow tailored representation of configurable criteria over time and across projects. The Vulnerability Heatmap is particularly helpful for Security Awareness and Security Champions programs by giving an easy consumable representation of the enterprise’s flaws. Best-practice guidance for incorporation in your Awareness program will be referenced in the future.
As this project is open source anyway, we had the idea of putting it into DefectDojo, but we are still in contact with its maintainers. They currently have a feature freeze because v3 will be rolled out soon.
Conclusion
At secureIO, we are committed to enhancing the tools and resources available to the cybersecurity community. Our contributions to OWASP DefectDojo reflect our dedication to improving security and helping the community.
Stay tuned for more updates as we continue to innovate and contribute to the open-source cybersecurity ecosystem.
Feel free to reach out to us if you have any questions or need help integrating these tools into your security workflow. We are always here to help you enhance your cybersecurity defenses!